In the ever-evolving world of digital currency, understanding the technical foundations of wallet security is paramount. The latest report, “An In-Depth Analysis of the BIP39 Protocol,” provides a comprehensive look at how mnemonic phrases are generated and transformed into private keys, securing digital assets with unparalleled precision.
Exploring Mnemonic Standards and Generation Techniques
The now standardized mnemonic dictionaries include Simplified Chinese, Traditional Chinese, English, Japanese, French, Italian, Korean, and Spanish. Mnemonics in the above languages can be generated, but most mainstream wallet practices still only use English.
Generally, the number of mnemonic words in a wallet is 12 or 24, but this standard can also generate 15, 18, 21 mnemonic words, or even less than 12 words. When developing a wallet, 24 words are generally used for security reasons, and 12 words are generally used for compatibility with other mainstream wallets or ease of use. If it is less than 12 words, the probability of collision is too high and the risk is too high. It is not recommended to use it.
Mnemonic phrase generation
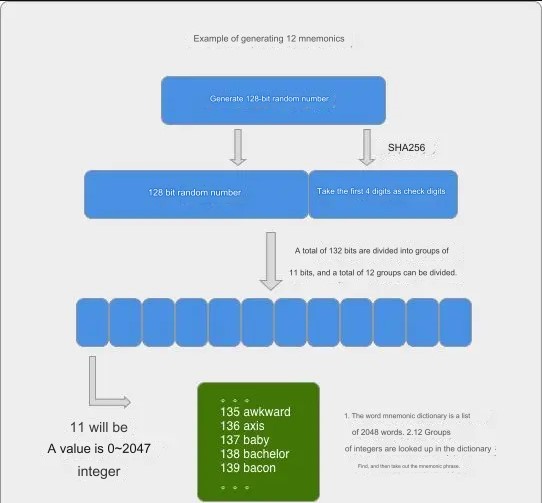
- Generate a random number of 128-256 Bit, but the number of digits in this random number must be a multiple of 32.
- Perform SHA256 on the random number and then take the first X bits as the check digit. The specific number depends on the number of digits to generate random numbers. (X = number of random digits / 32).
- Add the validation digit after the random number.
- Divide the random number with added validation digits into groups of 11 digits, and divide them into several groups.
- Then for every 11 digits, you can get a number with a value ranging from 0 to 2047. Based on these numbers, you can check the mnemonic dictionary to get the mnemonic word.
| Number of random digits | Number of check digits | Random number plus check digits | Number of mnemonics |
| 128 | 4 | 132 | 12 |
| 160 | 5 | 165 | 15 |
| 192 | 6 | 198 | 18 |
| 224 | 7 | 231 | 21 |
| 256 | 8 | 264 | 24 |
Generate private key from mnemonic phrase
1.Canonical encoding of mnemonics and salts using NFKD. (The salt is “mnemonic” + password)
2.Use the PBKDF2 algorithm to obtain a 512-bit seed. PBKDF2 uses HMAC-SHA512 as the hashing algorithm and performs 2048 calculations.
3.The first 256 bits are our private key. As for the function of the last 256 bits, we don’t need to know it for the time being. We will only use it when we use BIP32.
Things to pay attention to during development
During development, if you use Mnemonic Code Converter to generate mnemonic, and then use the mnemonic to generate a private key, the mnemonic may fail to be verified. But with a 24-word mnemonic phrase, the verification will not fail. Why is this? Generally, we use byte arrays or char arrays in development to store related data, but the minimum space occupied by a byte is one byte (8 bits), except for the 24 check digits of the mnemonic phrase. It can occupy 8 bits, but other mnemonic words occupy less than 8 bits. Many third-party libraries store 1 byte of check digits, but the data recovered from the mnemonic words is indeed missing. Then the verification is done based on byte comparison instead of comparing each bit, so there will be a problem of verification failure.
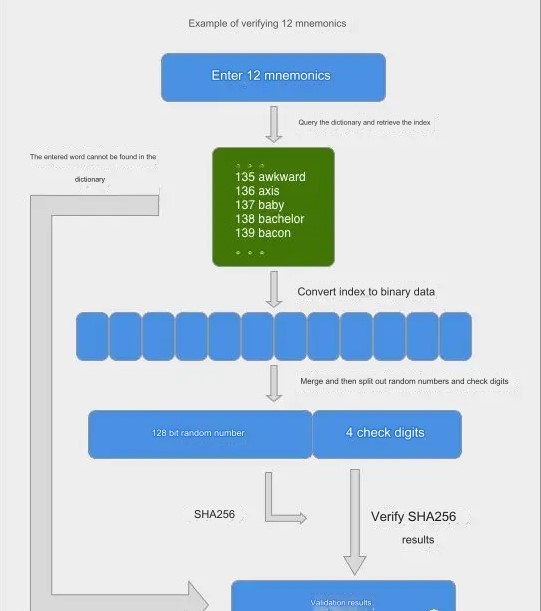
Verify the correctness of the mnemonic phrase
1.Go to the dictionary to look up words to see if the word entered by the user is in the dictionary.
2.Take out the indexes of all words and convert them into binary data composed of bits in order and then splice and combine them.
3.Split the binary data into random numbers and check digits, perform SHA256 on the random numbers and compare the check digit results to see if they are correct.
Some characteristics of mnemonics
1.Since the PBKDF2 algorithm of HMAC-SHA512 is used, the mnemonic cannot be deduced from the 512-bit seed in reverse.
2.Mnemonic words and 128-bit random numbers can be converted into each other, but they have no practical significance.
- When the mnemonic phrase generates a private key, you can add your own password to reduce the collision rate and improve security, but most domestic wallets do not support this feature.


